Overview
Travis CI is a continuous integration development platform that is being used by software teams in order to enable them to build, test and deploy applications easier and faster on multiple platforms. Travis CI runs on GitHub repositories, and it enforces security and licensing compliance in the CI/CD pipeline.
How It Works
To integrate Travis CI with WhiteSource, apply the following procedure:
Add or merge the following content to your '.travis.yml' file (usually it is located in the root directory of the repository):
NOTE: It is advised to use the below curl command only once a week to download the latest version of the Unified Agent for performance reasons and not as part of every build. You can do this using a scheduler task, such as cron.
Sample .travis.yml with WhiteSource integration
language: bash script: - bash <(curl -s -L https://github.com/whitesource/fs-agent-distribution/raw/master/standAlone/wss_agent.sh) -apiKey xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx -c [path to config file] -project travis-ci_test -d .This command runs the script 'wss_agent.sh'. It downloads the latest version of the WhiteSource Unified Agent Jar file and configuration file to your Travis CI host.
Afterwards, the script runs the Jar with the regular command line arguments of the Unified Agent.
Make sure to edit the Unified Agent configuration file to match your needs. See Unified Agent command line parameters for further information.
Use the API key and determine the name of the WhiteSource project.
2. Run the build. After the Travis CI build completes with a WhiteSource scan, you can review the scanning results in your WhiteSource organization.
Advanced Options
Policy Violations
You can fail builds in case of policy violation(s). To achieve this task, you can use the configuration file that you already defined to check policies. Use the configuration file ('-c parameter') with the following '.travis.yml' file:
Sample .travis.yml with WhiteSource integration
language: bash
script:
- bash <(curl -s -L https://github.com/whitesource/fs-agent-distribution/raw/master/standAlone/wss_agent.sh) -apiKey xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx -c [path to config file] -project travis-ci_test -d .
Your configuration file name should be different from 'whitesource-fs-agent.config'. The script ('wss_agent.sh') downloads the default file ('whitesource-fs-agent.config') and overrides your file when it has the same name.
Alternatively, you can use the following '.travis.yml' file:
This script downloads the default configuration file and changes its privacy policies values.
Sample .travis.yml with WhiteSource integration
language: bash
script:
# Download the latest version of WhiteSource FS Agent
- curl -LJO https://github.com/whitesource/fs-agent-distribution/raw/master/standAlone/whitesource-fs-agent.jar
# Download the default configuration file
- curl -LJO https://github.com/whitesource/fs-agent-distribution/raw/master/standAlone/whitesource-fs-agent.config
# Replace the flags in the configuration to enable policy check
- cat whitesource-fs-agent.config | sed -e "s/checkPolicies=false/checkPolicies=true/; s/forceCheckAllDependencies=false/forceCheckAllDependencies=true/" > temp_file.config
# Copy the new configuration file over the original file
- mv temp_file.config whitesource-fs-agent.config
# Run WhiteSource FS Agent
- java -jar whitesource-fs-agent.jar -apiKey xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx -c whitesource-fs-agent.config -d ~/ -project travisCI_test
The default configuration file may require further configuration modifications to suit your requirements.
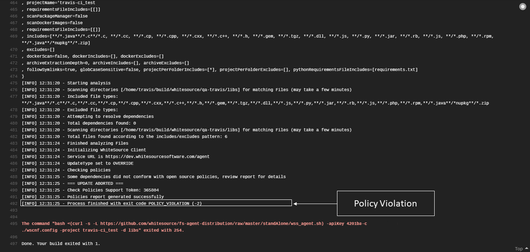
If there are policy violations, then the following message appears at the end of the "Job log" of Travis CI :
Process finished with exit code POLICY_VIOLATION (-2)
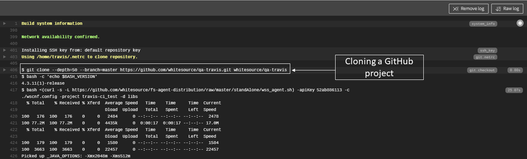
Sample of Usage on GitHub
The following screenshot illustrates cloning a GitHub project while using the Travis CI integration:
The following screenshot is an example of a policy violation: