...
| Table of Contents |
|---|
Overview
WhiteSource Remediate is a feature of WhiteSource's repository integrations, which automatically opens fix Pull Requests for vulnerable open-source components, upgrading them to the lowest non-vulnerable version.
WhiteSource Remediate is part of WhiteSource for Developers and integrated with WhiteSource for GitHub.com, WhiteSource for GitHub Enterprise, WhiteSource for Bitbucket Server, and WhiteSource for GitLab. In addition, Remediate is integrated with WhiteSource Renovate (see below for details). Renovate enables you to save time and reduce risk by automating dependency updates in software projects.
WhiteSource Remediate provides the following capabilities:
- Real-time monitoring - Runs continuously to detect the latest available fixes.
- Single-click fix - Generate automated fix Pull Requests on-demand or using custom workflow rules.
- Custom workflow rules - Open fix Pull Requests based on vulnerability severity or CVSS score.
- Annotated - Changelogs and commit histories are extracted and included when available.
- Dependency file discovery - Discovers and processes all dependency files in a repository.
- Lock-file support - Update lock files seamlessly in the same commit, including immediately resolving conflicts whenever PRs are merged.
NOTE: A fix Pull Request is only generated for security vulnerabilities discovered on your repo's default branch, and for direct dependencies only.
Supported Package Managers
...
Only SDK-style .csproj files are currently supported. By default, this includes:
- .NET Core 1.0 and above
- .NET Standard class libraries
- Any
.csprojin the SDK-style syntax
To convert your .NET Framework .csproj into an SDK-style project, follow this guide.
...
NOTE: In WhiteSource for GitLab, mirrored repositories are not supported.
WhiteSource Workflow Rules
WhiteSource Remediate is configured via custom Workflow Rules. To set up Workflow Rules for all or a selected list of WhiteSource Products/Projects, do as follows:
...
Once you set up a Workflow Rule, WhiteSource Remediate will start monitoring your selected repositories for vulnerable dependencies and generate corresponding fix Pull Requests.
Configuration of github.com credentials
| Info |
|---|
If you are running Remediate against github.com already, or making use of WhiteSource for github.com, then you don’t need to provision credentials explicitly. |
Regardless of which platform you are running on (GitHub.com or GitHub Server), Remediate can locate and embed open source Release Notes from projects hosted on github.com into Pull Requests. When Renovate functionality is enabled, Remediate may also need to fetch lists of tags and releases from github.com for other reasons (such as to check if a particular open-source package has any newer versions).
However, GitHub heavily rate limits any unauthenticated API requests to github.com, so if credentials are not available then Remediate will disable Release Notes fetching as well as github-tags, github-releases, and go datasources to ensure predictable behavior. Remediate will log a WARN message on startup if such credentials are missing.
For other use cases (including self-hosted GitHub Enterprise Server), to provide such credentials to the Remediate container, you should configure a github.com Personal Access Token into the environment variable GITHUB_COM_TOKEN. This token can belong to any github.com account and does needs only public read-only permissions. For details on creating such a token, click here.
WhiteSource cannot provide customers with a token for accessing github.com as that would go against that platform’s Terms of Service.
Providing the Integration Activation Key
WhiteSource Remediate can be configured to work with the integration activation key using either the prop.json configuration file or using environment variables.
NOTE: The environment variable takes precedence over an activation key value specified inside a prop.json file.
Providing the Integration Activation Key in prop.json
You can provide the integration's activation key to the Remediate container using a prop.json file.
Providing the Integration Activation Key using environment variables
You can provide the integration activation key by using the W4D_BOLT_OP_ACTIVATION_KEY environment variable inside the Remediate container.
Proxy Support
WhiteSource Remediate can be configured to work with proxy servers using either the prop.json configuration file or using environment variables.
Proxy Configuration in prop.json
When configuring proxies using prop.json, the "no proxy" list will be automatically configured to match the VCS endpoint in use (i.e. the GitHub, GitLab or Bitbucket Server endpoint). Internally Remediate will convert these to HTTP_PROXY, HTTPS_PROXY and NO_PROXY environment variables and pass them to child processes such as npm and composer.
Proxy Configuration Using Environment Variables
...
| Table of Contents |
|---|
Overview
WhiteSource Remediate automatically opens fix Pull Requests for vulnerable open-source components, upgrading them to the lowest non-vulnerable version. WhiteSource Remediate is part of WhiteSource Developer Integrations and integrated with WhiteSource for GitHub.com, WhiteSource for GitHub Enterprise, WhiteSource for Bitbucket Server, and WhiteSource for GitLab. Providing additional capabilities for project dependency health, Remediate is integrated with WhiteSource Renovate (see below for details). Renovate enables you to save time and reduce risk by automating dependency updates in software projects.
WhiteSource Remediate provides the following capabilities:
Real-time monitoring - Runs continuously to detect the latest available fixes.
Single-click fix - Generate automated fix Pull Requests on-demand or using custom workflow rules.
Custom workflow rules - Open fix Pull Requests based on vulnerability severity or CVSS score.
Annotated - Changelogs and commit histories are extracted and included when available.
Dependency file discovery - Discovers and processes all dependency files in a repository.
Lock-file support - Update lock files seamlessly in the same commit, including immediately resolving conflicts whenever PRs are merged.
NOTE: A fix Pull Request is only generated for security vulnerabilities discovered on your repo's base branches, including transitive dependencies in npm.
Supported Package Managers
Package Manager | Language | Extra Details |
|---|---|---|
Maven | Java | N/A |
Gradle | Java | N/A |
Go Modules | Golang | Remediate will update both the |
npm/Yarn | JavaScript | WhiteSource Remediate always updates both the package file (e.g. package.json) as well as any lock file (e.g. yarn.lock) in the same commit/fix Pull Request. |
NuGet | .NET | Only SDK-style
To convert your .NET Framework .csproj into an SDK-style project, follow this guide. |
pip | Python | N/A |
pipenv | Python | N/A |
poetry | Python | N/A |
setuptools | Python | N/A |
Composer | PHP | N/A |
NOTE: In WhiteSource for GitLab, mirrored repositories are not supported.
WhiteSource Workflow Rules
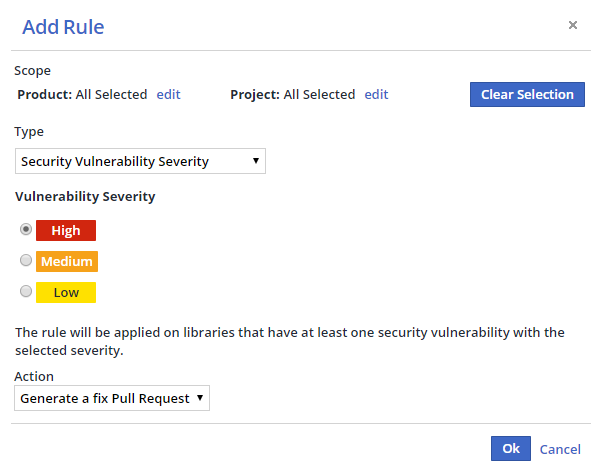
WhiteSource Remediate is configured via custom Workflow Rules. To set up Workflow Rules for all or a selected list of WhiteSource Products/Projects, do as follows:
From the WhiteSource web application, click the Integrate tab.
Expand the WhiteSource for Developers option.
From within the relevant repo integration settings, click Manage Workflow Rules. The Workflow Rules page is displayed.
Click Add Rule. The Add Rule dialog box is displayed.
Select a Product and/or Project scope from the Scope area or leave at the default (applies to all of your WhiteSource Products and Projects).
Select a rule type from the Type dropdown menu.
Click OK to create the rule.
Once you set up a Workflow Rule, WhiteSource Remediate will start monitoring your selected repositories for vulnerable dependencies and generate corresponding fix Pull Requests.
Configuration of GitHub.com Credentials
| Info |
|---|
If you are running Remediate against github.com already, or making use of WhiteSource for github.com, then you don’t need to provision credentials explicitly. |
Regardless of which platform you are running on (GitHub.com or GitHub Server), Remediate can locate and embed open source Release Notes from projects hosted on github.com into Pull Requests. When Renovate functionality is enabled, Remediate may also need to fetch lists of tags and releases from github.com for other reasons (such as to check if a particular open-source package has any newer versions).
However, GitHub heavily rate limits any unauthenticated API requests to github.com, so if credentials are not available then Remediate will disable Release Notes fetching as well as github-tags, github-releases, and go datasources to ensure predictable behavior. Remediate will log a WARN message on startup if such credentials are missing.
For other use cases (including self-hosted GitHub Enterprise Server), to provide such credentials to the Remediate container, you should configure a github.com Personal Access Token into the environment variable GITHUB_COM_TOKEN. This token can belong to any github.com account and does needs only public read-only permissions. For details on creating such a token, click here.
WhiteSource cannot provide customers with a token for accessing github.com as that would go against that platform’s Terms of Service.
Providing the Integration Activation Key
WhiteSource Remediate can be configured to work with the integration activation key using either the prop.json configuration file or using environment variables.
NOTE: The environment variable takes precedence over an activation key value specified inside a prop.json file.
Providing the Integration Activation Key in prop.json
You can provide the integration's activation key to the Remediate container using a prop.json file.
Providing the Integration Activation Key using Environment Variables
You can provide the integration activation key by using the W4D_BOLT_OP_ACTIVATION_KEY environment variable inside the Remediate container.
Proxy Support
WhiteSource Remediate can be configured to work with proxy servers using either the prop.json configuration file or using environment variables.
Proxy Configuration in prop.json
When configuring proxies using prop.json, the "no proxy" list will be automatically configured to match the VCS endpoint in use (i.e. the GitHub, GitLab or Bitbucket Server endpoint). Internally Remediate will convert these to HTTP_PROXY, HTTPS_PROXY and NO_PROXY environment variables and pass them to child processes such as npm and composer.
Proxy Configuration Using Environment Variables
WhiteSource Remediate also supports the industry convention of HTTP_PROXY, HTTPS_PROXY and NO_PROXY. This provides more flexibility if you need to also configure any internal/private registries in the no proxy list so is the recommended configuration approach. Such variables will be passed transparently to child processes.
Automated Dependency Updates for Improved Dependency Health
Although remediating vulnerabilities should be the highest priority for dependency updating, it is recommended to adopt a proactive dependency update approach using Remediate’s “Renovate” capabilities.
WhiteSource’s Renovate capabilities bring automated dependency updates to WhiteSource’s repository integrations. By enabling Renovate, more than 50 package manager formats can be detected automatically and dependencies within updated, including numerous Infrastructure as Code managers such as Terraform and Ansible.
The key advantages of automating dependency updates are:
Vulnerability fixes are often discretely released days or weeks prior to public disclosure, and you may be lucky enough to frequently update using Renovate prior to disclosure and avoid a vulnerability notification altogether
Even if projects are not completely up-to-date, being reasonably up-to-date means that applying vulnerability remediations is much lower risk and therefore can be done more quickly, lowering the average time-to-resolution for CVEs
For highly nested dependencies, such as Containers and Infrastructure as Code where vulnerable components may be deeply transitive, staying up-to-date (e.g. with Docker base image updates) is one of the best ways to stay secure anyway
Integration with WhiteSource Renovate
WhiteSource Renovate functionality can be enabled in WhiteSource Remediate via an option in the .whitesource configuration file.
With Renovate functionality enabled, Remediate will then raise PRs/MRs not only for vulnerable dependencies but also for outdated dependencies too.
Renovate is designed for users who aim to keep their dependencies up-to-date, primarily for the reasons of:
Keeping up with all bug-fixes from open source libraries
Reducing the risk of updating vulnerable versions in a hurry, because small jumps in versions are easier to test than large
Renovate itself is well-documented via its own documentation site. The Renovate docs are automatically generated based off the open source Renovate repository, so are unnecessary to duplicate here in full, however examples and clarifications will be provided below specifically for users of WhiteSource Remediate.
...
Renovate supports a range of different filenames, however for WhiteSource Remediate integration only the .whitesource configuration file is used. Renovate is disabled by default so enabled by setting remediateSettings.enableRenovate = true like so:
| Code Block |
|---|
{ |
...
"remediateSettings": { |
...
"enableRenovate": true |
...
} |
...
} |
Any configuration you place within the remediateSettings object will be used by Remediate similarly to how Renovate usually uses a renovate.json configuration file. Therefore, if you have an existing renovate.json file in a repository but are migrating to WhiteSource Remediate then you'd copy paste its contents inside remediateSettings before removing the renovate.json file.
...
If you are new to Renovate, we recommend you start with the config:base preset config, which enables functionality such as maximum two dependency update PRs per hour as well as grouping well-known monorepo dependencies together:
| Code Block |
|---|
{ |
...
"remediateSettings": { |
...
"enableRenovate": true, |
...
"extends": ["config:base"] |
...
} |
...
} |
What Happens When Remediations Are Available
...
Renovate is highly configurable with many options, so here are the most commonly used ones to take a look at first:
schedule: use this is you want to raise dependency update PRs during limited times, such as weeknights and weekends. Combine with timezone so that schedules can be written in your local time instead of UTC.
packageRules with groupName: matching multiple packages and assigning a groupName will mean they will be grouped into a single PR. This can be useful if certain packages must always be upgraded together, or if you wish to reduce the total number of PRs.
assignees and reviewers: use these fields to configure who is assigned or requested to review PRs (note: will apply to remediation PRs/MRs too)
automerge: enable this (ideally using packageRules) on dependencies you trust to be merged automatically by Remediate once they pass tests.
If you have questions about any particular configuration option or are looking for examples of its use, you may find it useful to search existing Issues in Renovate's Config Help Repository on GitHub.
...