...
| Table of Contents |
|---|
Overview
WhiteSource Remediate is a feature of WhiteSource's repository integrations, which automatically opens fix Pull Requests for vulnerable open-source components, upgrading them to the lowest non-vulnerable version.
...
| Table of Contents |
|---|
Overview
WhiteSource Remediate automatically opens fix Pull Requests for vulnerable open-source components, upgrading them to the lowest non-vulnerable version. WhiteSource Remediate is part of WhiteSource for Developers and integrated with WhiteSource for GitHub.com, WhiteSource for GitHub Enterprise, WhiteSource for Bitbucket Server, and WhiteSource for GitLab. In additionProviding additional capabilities for project dependency health, Remediate is integrated with WhiteSource Renovate (see below for details). Renovate enables you to save time and reduce risk by automating dependency updates in software projects.
WhiteSource Remediate provides the following capabilities:
...
NOTE: A fix Pull Request is only generated for security vulnerabilities discovered on your repo's default branch, and for direct dependencies onlybase branches, including transitive dependencies in npm.
Supported Package Managers
...
From the WhiteSource web application, click the Integrate tab.
Expand the WhiteSource for Developers option.
From within the relevant repo integration settings, click Manage Workflow Rules. The Workflow Rules page is displayed.
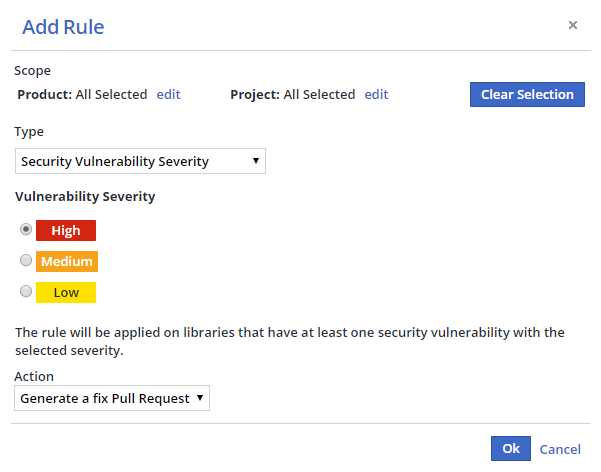
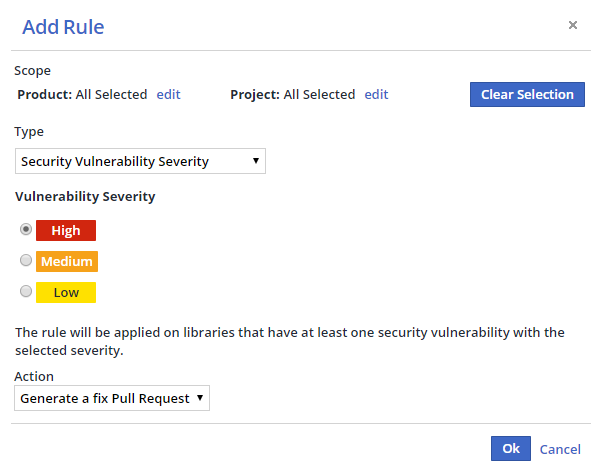
Click Add Rule. The Add Rule dialog box is displayed.
Select a Product and/or Project scope from the Scope area or leave at the default (applies to all of your WhiteSource Products and Projects).
Select a rule type from the Type dropdown menu.
Click OK to create the rule.
Once you set up a Workflow Rule, WhiteSource Remediate will start monitoring your selected repositories for vulnerable dependencies and generate corresponding fix Pull Requests.
Configuration
...
of GitHub.
...
com Credentials
| Info |
|---|
If you are running Remediate against github.com already, or making use of WhiteSource for github.com, then you don’t need to provision credentials explicitly. |
...
WhiteSource Remediate can be configured to work with the integration activation key using either the prop.json configuration file or using environment variables.
NOTE: The environment variable takes precedence over an activation key value specified inside a prop.json file.
Providing the Integration Activation Key in prop.json
You can provide the integration's activation key to the Remediate container using a prop.json file.
Providing the Integration Activation Key using
...
Environment Variables
You can provide the integration activation key by using the W4D_BOLT_OP_ACTIVATION_KEY environment variable inside the Remediate container.
Proxy Support
WhiteSource Remediate can be configured to work with proxy servers using either the prop.json configuration file or using environment variables.
...
WhiteSource Remediate also supports the industry convention of HTTP_PROXY, HTTPS_PROXY and NO_PROXY. This provides more flexibility if you need to also configure any internal/private registries in the no proxy list so is the recommended configuration approach. Such variables will be passed transparently to child processes.need to also configure any internal/private registries in the no proxy list so is the recommended configuration approach. Such variables will be passed transparently to child processes.
Automated Dependency Updates for Improved Dependency Health
Although remediating vulnerabilities should be the highest priority for dependency updating, it is recommended to adopt a proactive dependency update approach using Remediate’s “Renovate” capabilities.
WhiteSource’s Renovate capabilities bring automated dependency updates to WhiteSource’s repository integrations. By enabling Renovate, more than 50 package manager formats can be detected automatically and dependencies within updated, including numerous Infrastructure as Code managers such as Terraform and Ansible.
The key advantages of automating dependency updates are:
Vulnerability fixes are often discretely released days or weeks prior to public disclosure, and you may be lucky enough to frequently update using Renovate prior to disclosure and avoid a vulnerability notification altogether
Even if projects are not completely up-to-date, being reasonably up-to-date means that applying vulnerability remediations is much lower risk and therefore can be done more quickly, lowering the average time-to-resolution for CVEs
For highly nested dependencies, such as Containers and Infrastructure as Code where vulnerable components may be deeply transitive, staying up-to-date (e.g. with Docker base image updates) is one of the best ways to stay secure anyway
Integration with WhiteSource Renovate
WhiteSource Renovate functionality can be enabled in WhiteSource Remediate via an option in the .whitesource configuration file.
With Renovate functionality enabled, Remediate will then raise PRs/MRs not only for vulnerable dependencies but also for outdated dependencies too.
Renovate is designed for users who aim to keep their dependencies up-to-date, primarily for the reasons of:
...