...
| Table of Contents |
|---|
General Information
JFrog Xray works with JFrog Artifactory to perform universal analysis of binary software components at any stage of the application lifecycle.
The WhiteSource Xray integration is a vulnerability feed that can be easily integrated with your Xray account.
...
| Info |
|---|
Your organization API key is available on the Integrate tab of your WhiteSource account, under Integration. |
Setting Up the WhiteSource Integration
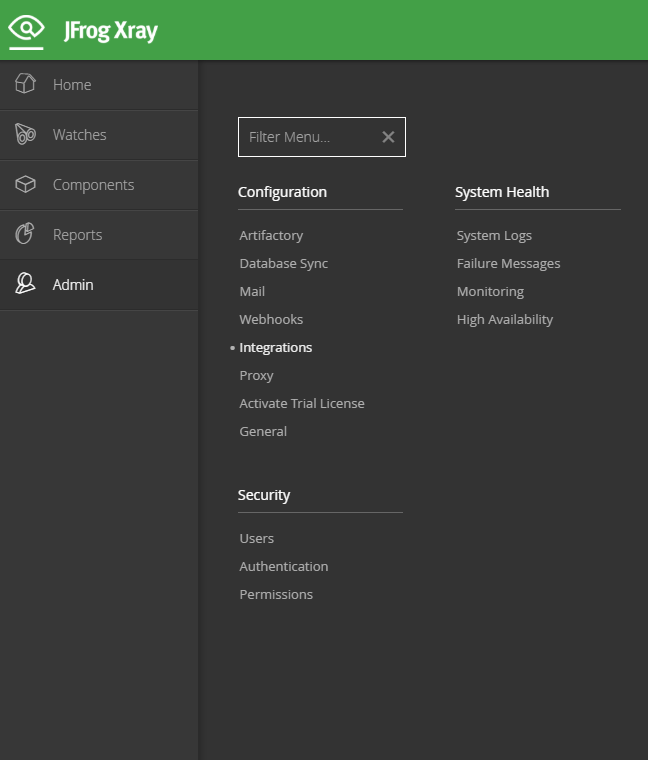
Login to JFrog Xray with administrator permissions. From the main menu, select
Admin →Admin > Configuration
→ Integrations> Integrations.
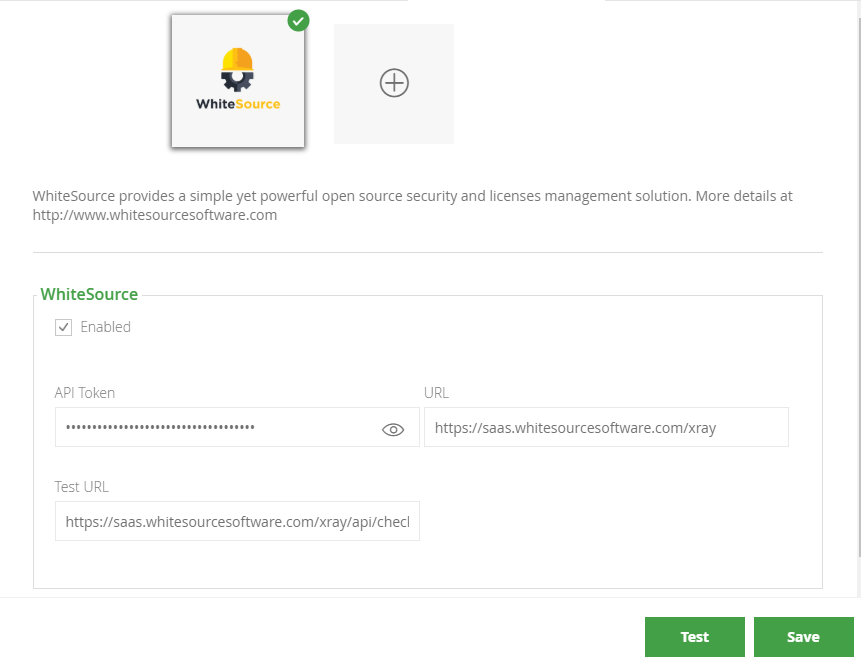
The integration pop-up window appears. Select the WhiteSource icon from the integration list, and enter the WhiteSource API key in the 'API Token' field.
is
The test URLis https://saas.whitesourcesoftware.com/xray/api/checkauth
oror in Azure
EUEU https://app-eu.whitesourcesoftware.com/xray/api/checkauth.
| Info |
|---|
The URL for an on-premises deployment is the on- |
...
premises installation URL. |
Testing & Saving the Integration
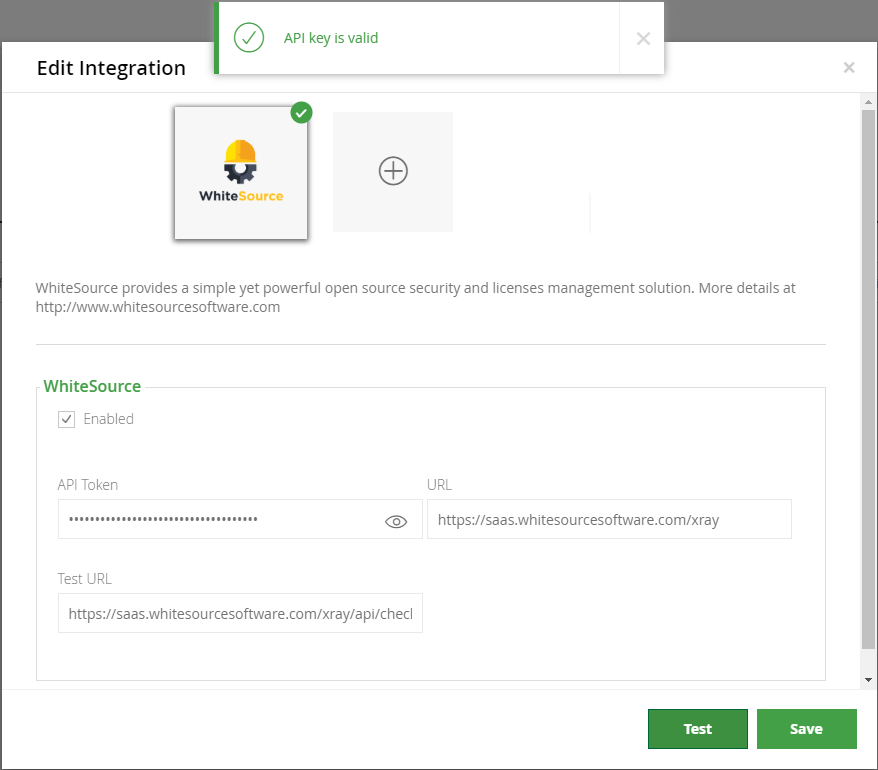
Click
onthe
'Test
'button to validate that the integration is configured properly. A confirmation message should appear indicating that the API key is valid.
Click
on the 'Save
' button.
Viewing Security Vulnerabilities
Once integrated, Xray starts pulling data from WhiteSource based on your watches (rules).
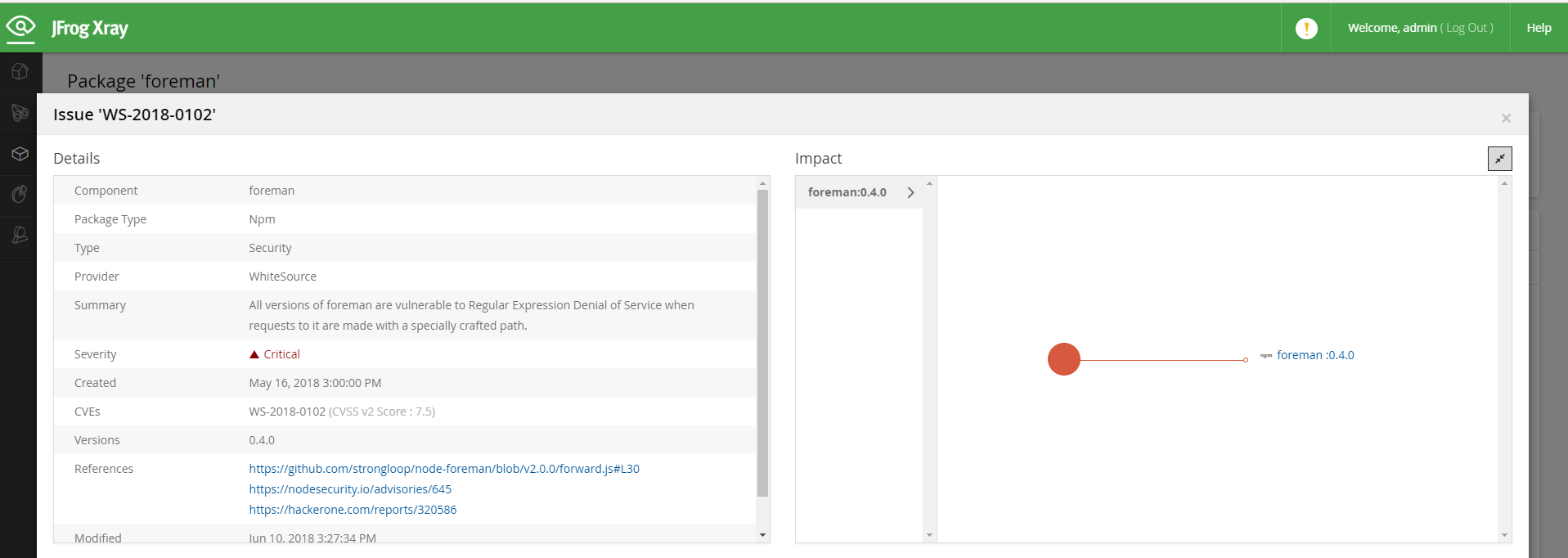
WhiteSource provides all relevant information about security vulnerabilities (severity, impacted versions and actionable remediation suggestions), and known severe software bugs for each of the displayed open source components. To view vulnerabilities:
Go to the Security tab of a specific package as displayed in the following screenshot:
Select a specific component in order to view details on the security vulnerability.