| Table of Contents |
|---|
...
WhiteSource Remediate is part of WhiteSource for Developers and integrated with WhiteSource for GitHub.com, WhiteSource for GitHub Enterprise, WhiteSource for Bitbucket Server, and WhiteSource for GitLab. In addition, Remediate is integrated with WhiteSource Renovate (see below for details). Renovate enables you to save time and reduce risk by automating dependency updates in software projects.
WhiteSource Remediate provides the following capabilities:
...
- From the WhiteSource web application, click the Integrate tab.
- Expand the WhiteSource for Developers option.
- From within the relevant repo integration settings, click Manage Workflow Rules. The Workflow Rules page is displayed.
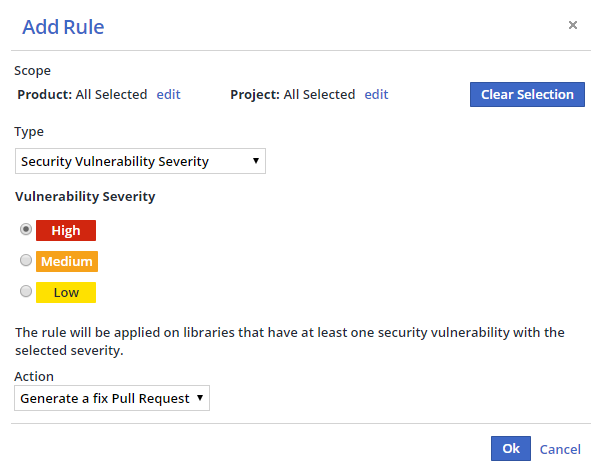
- Click Add Rule. The Add Rule dialog box is displayed.
- Select a Product and/or Project scope from the Scope area or leave at the default (applies to all of your WhiteSource Products and Projects).
- Select a rule type from the Type dropdown menu.
- Click OK to create the rule.
Once you set up a Workflow Rule, WhiteSource Remediate will start monitoring your selected repositories for vulnerable dependencies and generate corresponding fix Pull Requests.
Configuration of github.com credentials
| Info |
|---|
If you are running Remediate against github.com already, or making use of WhiteSource for GitHubgithub.com, then you don’t need to provision credentials explicitly. |
Regardless of which platform you are running on (GitHub.com or GitHub Server), Remediate can locate and embed open source Release Notes from projects hosted on github.com into Pull Requests. When Renovate functionality is enabled, Remediate may also need to fetch lists of tags and releases from github.com for other reasons (such as to check if a particular open-source package has any newer versions).
However, GitHub heavily rate limits any unauthenticated API requests to github.com, so if credentials are not available then Remediate will disable Release Notes fetching as well as github-tags, github-releases, and go datasources to ensure predictable behavior. Remediate will log a WARN message on startup if such credentials are missing.
For other use cases (including self-hosted GitHub Enterprise Server), to provide such credentials to the Remediate container, you should configure a github.com Personal Access Token into the environment variable GITHUB_COM_TOKEN. This token can belong to any github.com account and does needs only public read-only permissions. For details on creating such a token,
...
click here.
WhiteSource cannot provide customers with a token for accessing github.com as that would go against that platform’s Terms of Service.
Proxy Support
WhiteSource Remediate can be configured to work with proxy servers using either the prop.json configuration file or using environment variables.
...
WhiteSource Remediate also supports the industry convention of HTTP_PROXY, HTTPS_PROXY and NO_PROXY. This provides more flexibility if you need to also configure any internal/private registries in the no proxy list so is the recommended configuration approach. Such variables will be passed transparently to child processes.
Integration with WhiteSource Renovate
WhiteSource Renovate functionality can be enabled in WhiteSource Remediate, currently for WhiteSource for GitHub Enterprise and WhiteSource for GitLab only.
With Renovate functionality enabled, Remediate will then raise PRs/MRs not only for vulnerable dependencies but also for outdated dependencies too.
Renovate is designed for users who aim to keep their dependencies up-to-date, primarily for the reasons of:
...